

William Morgan
November 6, 2025
Today we’re happy to announce that Linkerd will soon have official support for Model Context Protocol (MCP). We’ll be giving scheduled MCP+Linkerd demos at KubeCon, or, if you won't be there, you can sign up for our MCP early access program for a sneak peek.
What is MCP and why should you care?
MCP is a protocol for agentic traffic that is rapidly becoming essential for AI workflows. It is the core mechanism by which agentic workloads access resources such as internal and external APIs. While MCP adoption has bloomed in specific developer use cases, in the enterprise, broader adoption of MCP has been hindered by significant gaps in operational requirements. And while one the wire MCP on the wire is “just” HTTP (plus JSON-RPC plus some extras), the information that’s critical to bridge these gaps is not attainable through standard HTTP parsing mechanisms.
Our goal is to bring sanity to agentic traffic in the enterprise. To do this, Linkerd solves two critical challenges for enterprise MCP adoption. First, observability: What MCP traffic is running on the cluster? Where is it coming from? Where is it going? What calls are being made? How hard is this traffic hitting my existing API servers? Today, MCP traffic is largely opaque in Kubernetes, with little to no visibility into usage and impact.
Second, security: How do I ensure that agentic workloads are only able to access allowed services? And within those services, are only able to call allowed methods? (For example, you may want to protect the “drop the database” API call from agentic access, lest you also end up with an entry in the AI Darwin Awards.) Today, agentic traffic is given the same security profile as “regular traffic”—despite the fact its security profile area is completely different.
In keeping with Linkerd’s design philosophy, we’ve tackled these in a way that “just works”. Every meshed MCP server, regardless of what it does or what language it’s written in, automatically gets fine-grained metrics (including error rate, volume, latency, etc per individual tool/resource/prompt); distributed tracing capabilities; and zero-trust access control (again, per tool/resource/prompt and per agent identity) that is controlled via existing AuthorizationPolicy CRDs. In other words: observing and securing an MCP server is now almost exactly like observing and securing anything else.
Show me
Here’s an example of the Linkerd dashboard showing the full list of MCP tools, prompts, and resources discovered for an MCP server detected on the cluster:
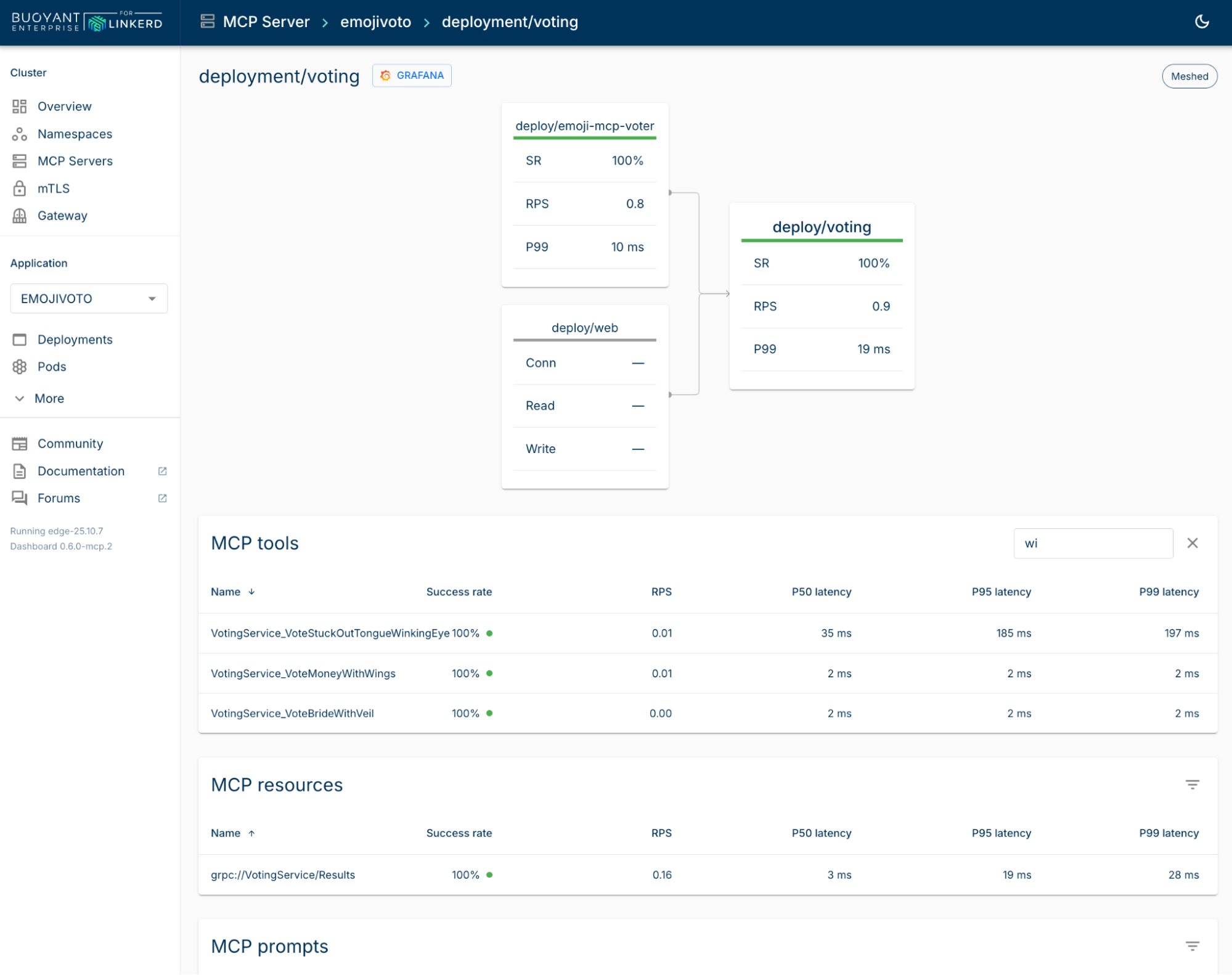
Of course, we can also dive into specific workloads and metrics in our standard metrics stack—here’s an example of visualizing MCP tool latency in Grafana, alongside a list of unauthorized calls that were automatically denied by Linkerd on the left.
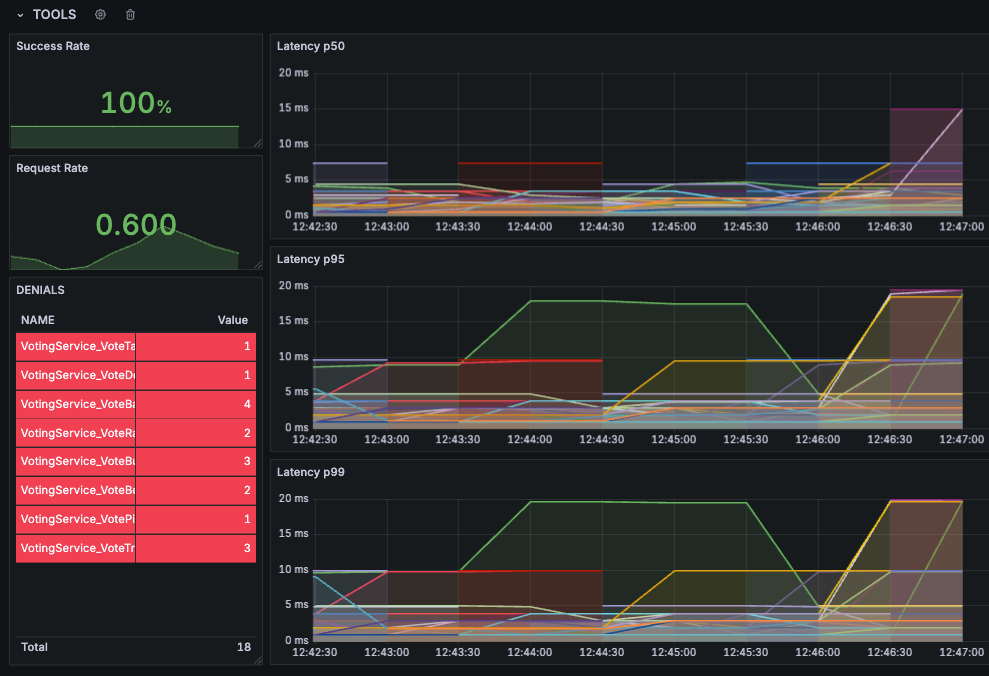
Drop Linkerd into your cluster and this is exactly the kind of visibility and control that you get over your MCP traffic.
What’s next?
MCP support gives Linkerd the ability to provide its users with some powerful guarantees: that any MCP server deployed on the cluster, regardless of what it does and how it works, will automatically have Linkerd’s full suite of observability available, and can be secured with Linkerd’s zero trust authorization policies. In other words, that MCP servers on your cluster can be, by default, both fully observable and secure from unauthorized access.
But this is just a first step in a broader plan. We’ve been spending most of this year deep in conversation with our customers, exploring the evolution of agentic workloads in the enterprise. One thing that’s clear is that things are moving fast and no one has a convincing picture of what the “final form” of a truly AI-enabled enterprise looks like. The MCP usage we see today is just one use case—and even here, MCP in the enterprise requires handling tough challenges that Linkerd doesn’t help with (yet!) like prompt injection, data exfiltration, user-level authorization, and more. Beyond that, there’s A2A, UTCP, and a thousand other avenues of exploration and development.
But it’s also clear to us that regardless of the details, the sheer volume of agentic traffic is poised to grow exponentially, even in restrictive enterprise environments. And, much like the “microservices revolution” that formed the primordial soup from which Kubernetes and Linkerd first sprung, agentic usage will be unpredictable and unconstrained, and will require thoughtful, well-designed, and platform-level solutions to truly tackle at scale.
So while MCP support in Linkerd is a clear win, it’s just one part of the broader solution, and just one part of a broader body of really exciting work that Buoyant is working on in this area—hand in hand with our customers. Stay tuned for much, much more.
Getting started
MCP support will be available in upcoming Linkerd releases (including the enterprise version of Linkerd, Buoyant Enterprise for Linkerd). We’ll be demoing this feature at KubeCon NA in Atlanta next week at booth 440, or sign up for our MCP early access program to get a sneak peek.








 LinkedIn
LinkedIn